Understanding Linux file permissions (how to find them, read them, and change them) is an important part of maintaining and securing your systems.
File Permissions
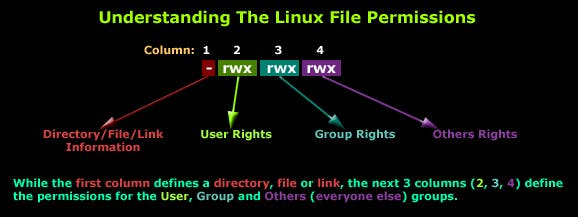
The Linux filesystem gives us three types of permissions. Here is a simplified review:
User (or user owner)
Group (or owner group)
Other (everyone else)
With these permissions, we can grant three (actually five, but we’ll get to that in a minute) types of access:
Read
Write
eXecute
The concept of Linux File permission and ownership is important in Linux. Here, we will be working on Linux permissions and ownership and will do tasks on both of them. Let us start with the Permissions.
Create a simple file and do
ls -ltrto see the details of the files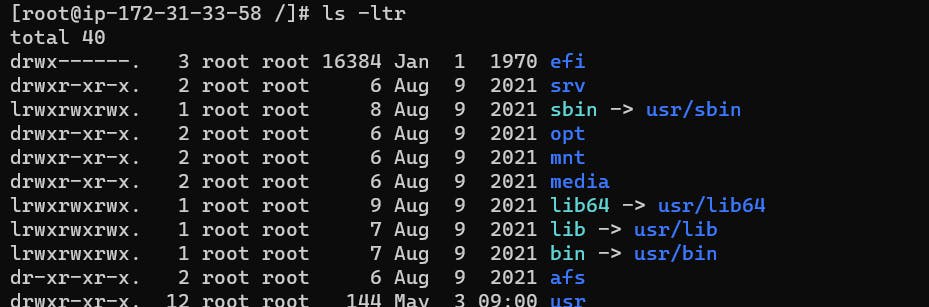
Each of the three permissions are assigned to three defined categories of users. The categories are:
owner — The owner of the file or application.
"chown" is used to change the ownership permission of a file or directory.
chown ec2-user script.sh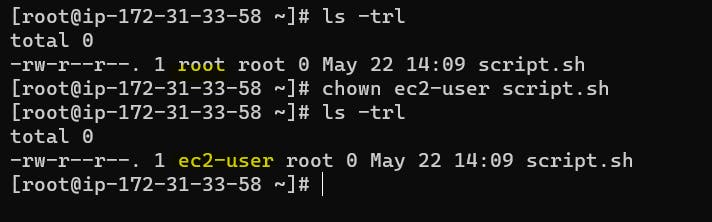
How do you modify Linux file permissions?
You can modify file and directory permissions with the chmod command, which stands for "change mode." To change file permissions in numeric mode, you enter chmod and the octal value you desire, such as 744, alongside the file name. To change file permissions in symbolic mode, you enter a user class and the permissions you want to grant them next to the file name. For example:
$ chmod ug+rwx example.txt
$ chmod o+r example2.txt
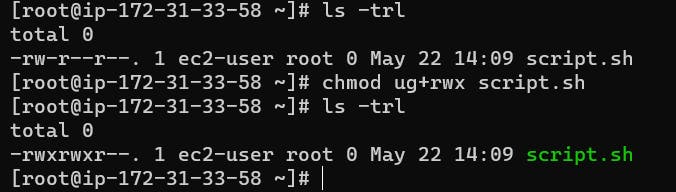
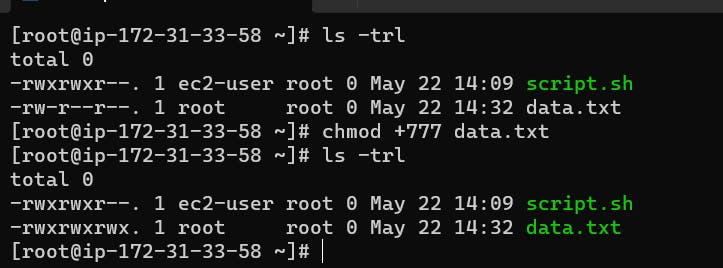
This grants read, write, and execute for the user and group, and only read for others. In symbolic mode, chmod u represents permissions for the user owner, chmod g represents other users in the file's group, chmod o represents other users not in the file's group. For all users, use chmod a.
What are special file permissions?
Special permissions are available for files and directories and provide additional privileges over the standard permission sets that have been covered.
SUID is the special permission for the user access level and always executes as the user who owns the file, no matter who is passing the command.
SGID allows a file to be executed as the group owner of the file; a file created in the directory has its group ownership set to the directory owner. This is helpful for directories used collaboratively among different members of a group because all members can access and execute new files.
The "sticky bit" is a directory-level special permission that restricts file deletion, meaning only the file owner can remove a file within the directory.
Access Control Lists
What is ACL?
Access control list (ACL) provides an additional, more flexible permission mechanism for file systems. It is designed to assist with UNIX file permissions. ACL allows you to give permissions for any user or group to any disc resource.
Use of ACL :
Think of a scenario in which a particular user is not a member of group created by you but still, you want to give some read or write access, how can you do it without making the user a member of the group, here comes in picture Access Control Lists, ACL helps us to do this trick.
Basically, ACLs are used to make a flexible permission mechanism in Linux.
setfacl and getfacl are used for setting up ACL and showing ACL respectively.
For example :
getfacl test/declarations.h
Output:
# file: test/declarations.h
# owner: mandeep
# group: mandeep
user::rw-
group::rw-
other::r--
List of commands for setting up ACL :
1) To add permission for user
setfacl -m "u:user:permissions" /path/to/file
2) To add permissions for a group
setfacl -m "g:group:permissions" /path/to/file
3) To allow all files or directories to inherit ACL entries from the directory it is within
setfacl -dm "entry" /path/to/dir
4) To remove a specific entry
setfacl -x "entry" /path/to/file
5) To remove all entries
setfacl -b path/to/file
For example :
setfacl -m u:mandeep:rwx test/declarations.h
Modifying ACL using setfacl :
To add permissions for a user (user is either the user name or ID):
# setfacl -m "u:user:permissions"
To add permissions for a group (group is either the group name or ID):
# setfacl -m "g:group:permissions"
To allow all files or directories to inherit ACL entries from the directory it is within:
# setfacl -dm "entry"
Example :
setfacl -m u:mandeep:r-x test/declarations.h
Using Default ACL :
The default ACL is a specific type of permission assigned to a directory, that doesn’t change the permissions of the directory itself, but makes so that specified ACLs are set by default on all the files created inside of it. Let’s demonstrate it : first we are going to create a directory and assign default ACL to it by using the -d option:
$ mkdir test && setfacl -d -m u:dummy:rw test
Happy Learning Thanks for reading my article. Have a nice day.
For updates follow me on LinkedIn: Swapnil Khairnar
Hashtags:
#90daysofdevops #devops #cloud #aws #awscloud #awscommunity #docker #linux #kubernetes #k8s #ansible #grafana #terraform #github #opensource #90daysofdevops #challenge #learningprogress #freelancer #linkedin #trainwithshubham #devopscommunity #cloudproviders #bash #bashshellscripting #awkward #shellscripting